Create Policies
Policies are what grant users access to Resources.
To define a Policy, go to Policies -> Add Policy.
Policies define a single Group's access to a single Resource.
Note: To preserve audit trails, Policy details cannot be changed once a Policy is created. Double-check to ensure the Group, Resource, and/or conditions are correct before creating the Policy.
Conditional access policies
On Team and higher plans, you may restrict access further based on the below conditions.
Client location
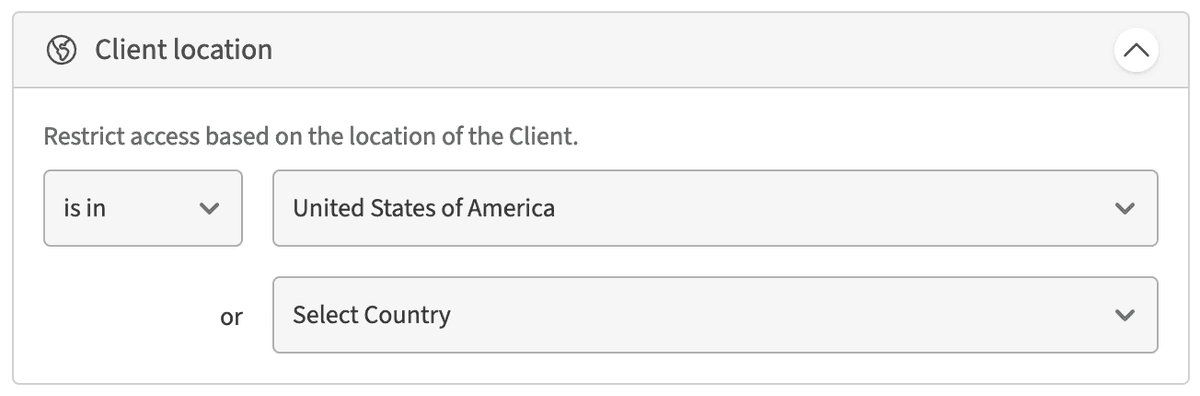
Restrict access only to Clients connecting from specific countries. When this is specified, the Client's IP address will be used to lookup the country of origin.
Client IP address or CIDR
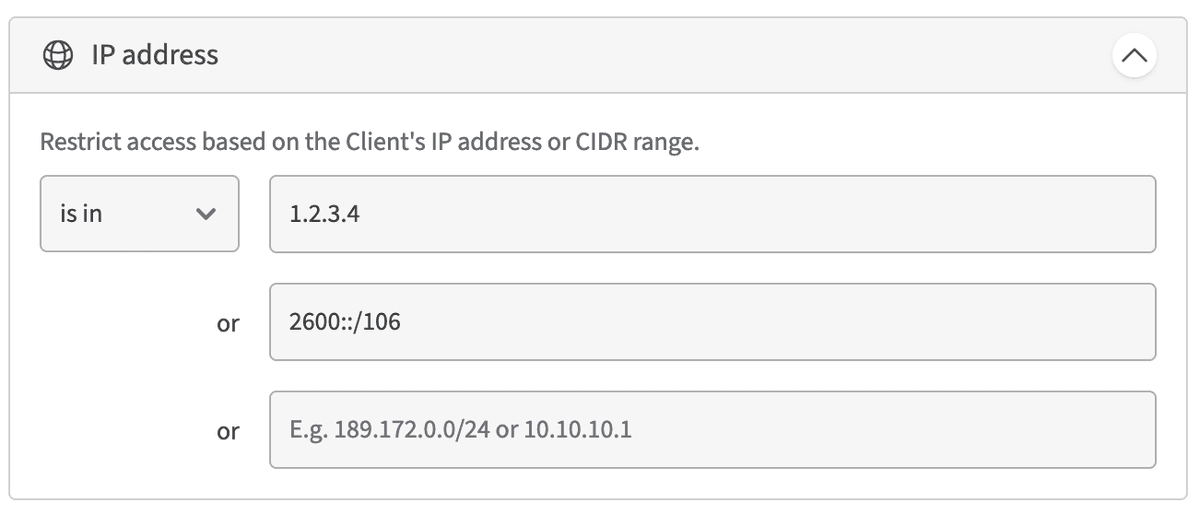
Restrict access to a specific IP address or range of Client IP addresses.
Identity provider
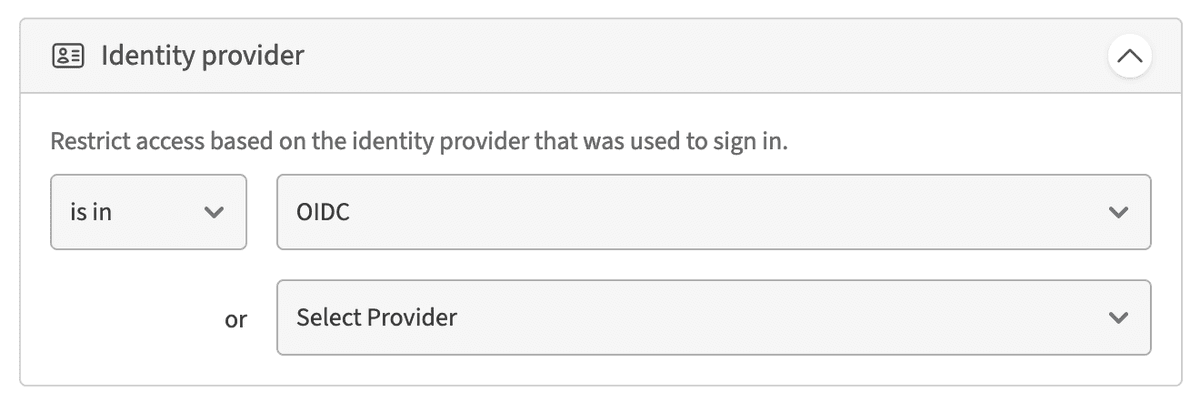
Restrict access based on the authentication provider that was used to authenticate the Client. This is useful when you want to apply a stricter set of authentication requirements for certain Groups or Resources using a separate SSO app in your identity provider.
Client verification
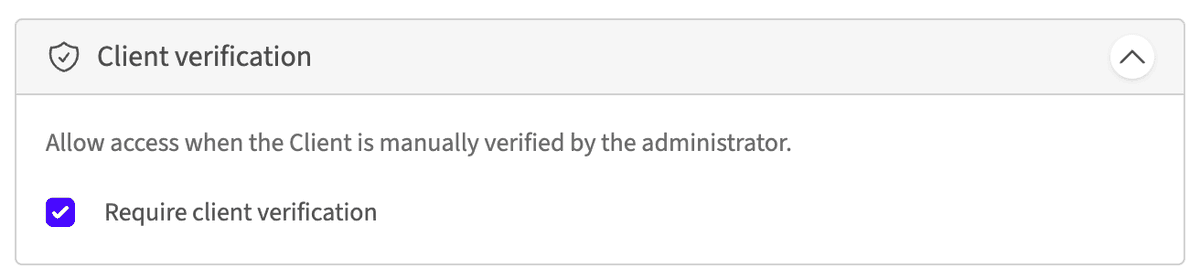
Restrict access only to verified Clients. When enabled, any Client being used by the Actors in the group will not be able to access the Resource unless it has been explicitly marked as verified in the admin portal.
The Client is identified for verification by their unique device IDs, which are retrieved from the following sources depending on the platform:
| Platform | Source | Notes |
|---|---|---|
| MacOS | Hardware ID | Matches the hardware ID found in the system report |
| MacOS | Hardware serial | Matches the hardware serial found in the system report |
| iOS | App installation ID | A unique UUIDv4 generated by the system upon app installation. Note: This ID will be reset if the app is uninstalled and reinstalled. |
| Android | App installation ID | A unique UUIDv4 generated by the system upon app installation. Note: This ID will be reset if the app is uninstalled and reinstalled. |
| Windows, Linux | Device ID | The BIOS UUID retried from SMBIOS |
| Windows, Linux | Motherboard serial | The mainboard serial retried from SMBIOS |
This feature acts as a lightweight device management solution, ideal for organizations looking to enforce device policies (e.g., preventing mobile device access to production databases) without requiring a full-fledged MDM system to be in place.
Time of day
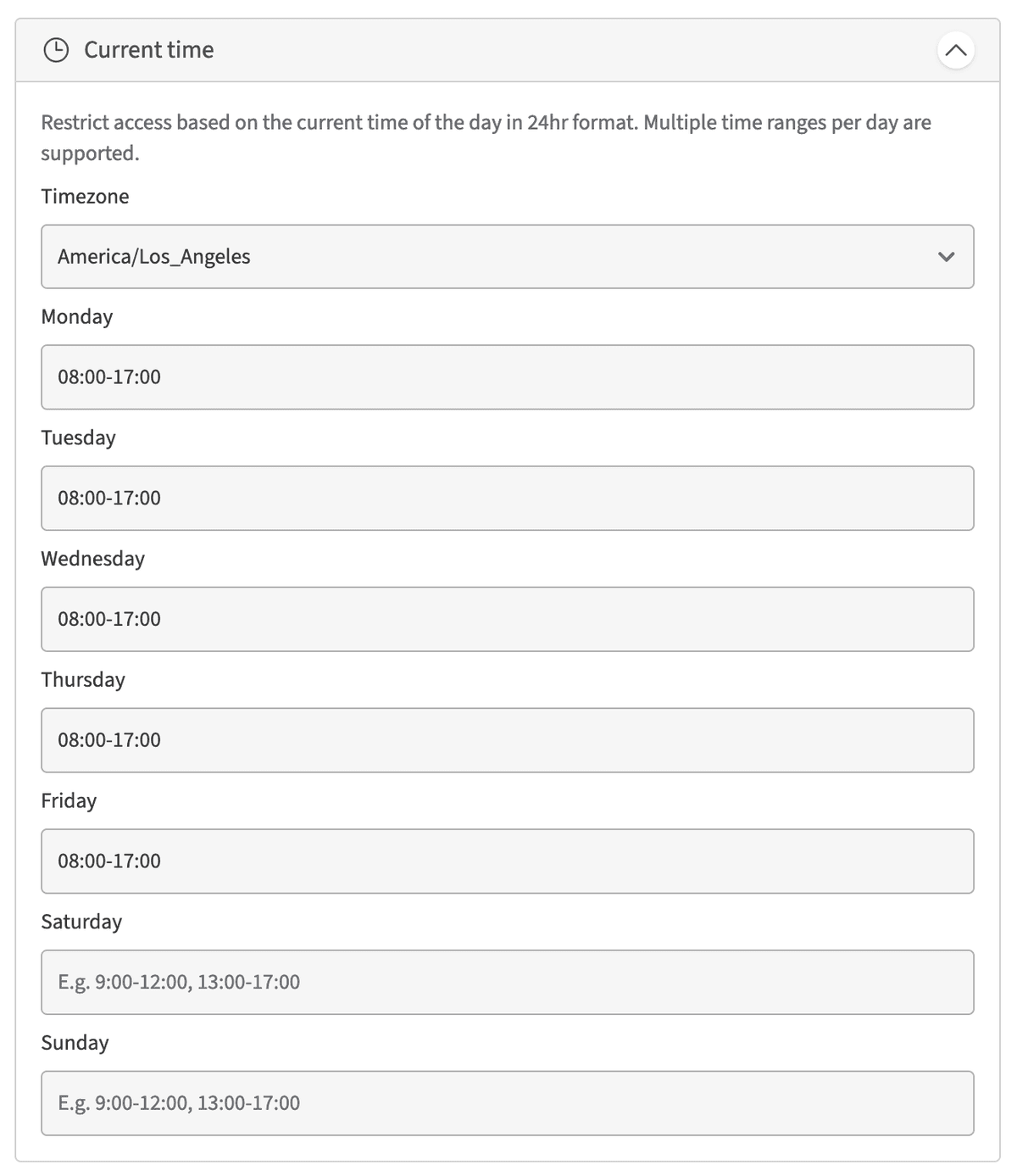
Restrict access to certain time windows throughout the week based on the 24hr time and specified time zone.
The time zone determines the offset used when determining whether to allow
access for a particular Client. For example, if you specify a time window of
08:00-17:00 and time zone of Eastern, Clients in the Pacific timezone 3
hours behind will be allowed access from 05:00-14:00 Eastern time.
How conflicting policies are resolved
The policy engine resolves access on a boolean OR basis. That means when two or more policies with conflicting conditions apply to a given Actor-Resource pair, access will be allowed to the Resource if any of the policies evaluate true.
As an example, consider the following policies:
| Policy | Group | Resource | Condition |
|---|---|---|---|
A | Engineering | Production DB | Time of day: 08:00-17:00 |
B | DevOps | Production DB | None |
If an Actor is a member of both the Engineering and DevOps groups, they will be
able to access the Production DB at any time of day since Policy B will always
evaluate to true.
Need additional help?
See all support options or try asking on one of our community-powered support channels:
- Discussion forums: Ask questions, report bugs, and suggest features.
- Discord server: Join discussions, meet other users, and chat with the Firezone team
- Email us: We read every message.